Fully Homomorphic Encryption – A Deep Dive into the Basics
Fully Homomorphic Encryption (FHE) is a cryptographic technique that is considered the holy grail of cryptography as it allows for analytical functions to be run directly on encrypted data. Thus, FHE has the potential to unlock huge untapped information resources – encrypted for privacy – and its real-world rollout is expected to deliver enormous benefits in fields like healthcare, finance and commerce, without compromising sensitive or private data.
At the time of writing, FHE is becoming increasingly practical, with companies offering pure-software solutions for specific applications. However, evaluating complex functions such as AI models, large-scale database queries or high-performance computing applications remain impractical due to computational overhead. However, Chain Reaction is well on the way to solving this issue with the development of an ASIC that accelerates FHE computations by orders of magnitude, enabling real-time deployment. 3PU™, Chain Reaction’s privacy processor is designed to enable real-time FHE deployment in cloud environments and AI models, ensuring continuous data privacy.
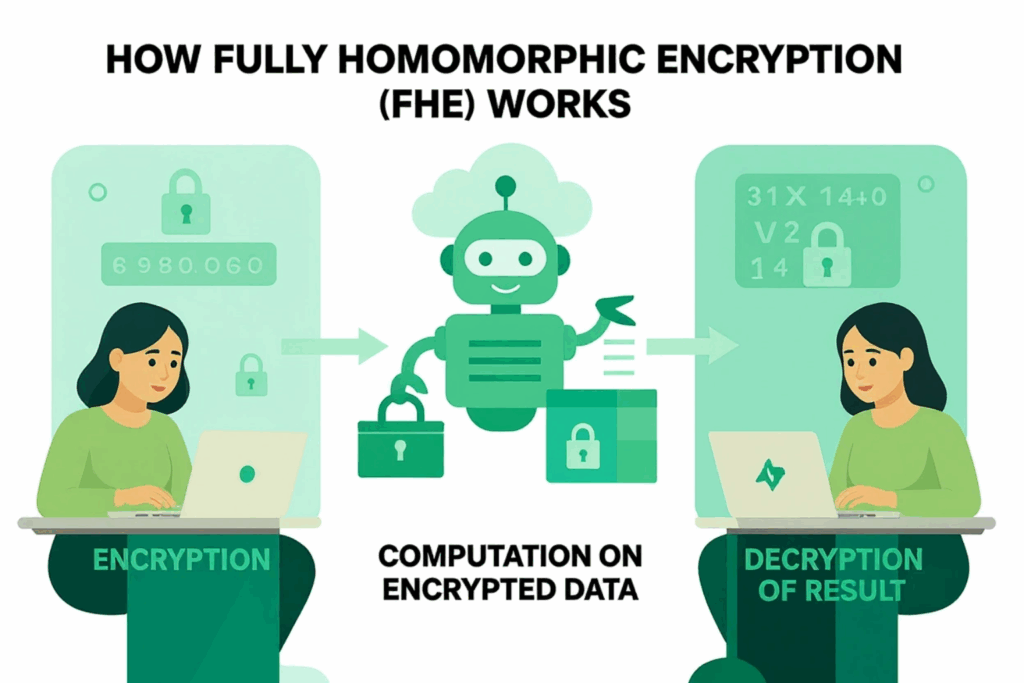
The Concept of FHE
FHE, The Core Concept
Data security tools and practices have advanced significantly in recent years. Yet despite this progress, data leaks and breaches continue to occur at alarming rates. For example, in June 2025, UBS confirmed that a cyberattack on its suppliers resulted in the leak of thousands of employees records, and according to Privacy Rights Clearinghouse, the first quarter of 2025 alone saw 658 distinct breaches affecting more than 32 million people.
While organizations are locking down private data, either at the enterprise level or on end-user devices, the unintended consequence is that valuable private datasets remain inaccessible. This limits the ability to extract insights and generate societal value from them.
What if researchers and data-driven organizations could use securely locked data without exposing any sensitive or personal information? With FHE, private data remains encrypted at all stages (at rest, in transit, and in use) while still allowing computations that generate insights, accessible only to those with the private key.
The History Of FHE
The underlying cryptographic technology is based on a concept called ‘privacy homomorphism’ which first gained traction in academic circles in the early 1970s.
Still in the pre-FHE era, in 1977, the foundation of the RSA cryptosystem, named after developers Ron Rivest, Adi Shamir, and Leonard Adleman, would become a pivotal moment in the timeline. The RSA cryptosystem was the first to exhibit partially homomorphic encryption, where “multiplying two encrypted with the same key is equivalent to raising the product of the plaintexts to the power of the secret key,” sums up IEEE.org.
A year later, Rivest and Adleman proposed, alongside Mike Dertouzos, that homomorphic encryption could be used to protect the security of stored data. This became a key driver to the development of FHE.
In 2009, there was a significant breakthrough on the road to FHE with the arrival of the first secure encryption scheme which allowed for unbounded addition and multiplication operations on encrypted data. Craig Gentry spearheaded this development by applying lattice-based cryptography. Gentry, alongside other researchers and organizations would quickly build advances to shift FHE from concept to practicality.
Since Gentry’s milestone breakthrough we have seen several FHE schemes developed, each with its own strengths and weaknesses. Later in our blog series you will be able to deep dive into the BGV (where the ‘G’ is for Gentry), BFV, CKKS, and TFHE schemes, and read our analysis of their features, and applications.
Probably the only tradeoff in the move from HE to FHE was in the significant computational overhead. This would become an even greater hurdle as we moved into the era of big data.
The Significance Of FHE In Modern Cryptography
Readers were introduced to some of the most significant benefits FHE can deliver to both individuals and organizations in our introduction. However, with researchers, governments, and the tech industry discovering the promise of big data in the 2010s, and the potential seen in using large data sets for machine learning and AI in the 2020s, FHE’s power to revolutionize data privacy could now be even more important for modern cryptography.
What Operations Are Possible With FHE?
Talking in mathematical terms, the latest generation FHE technologies facilitate the use of whatever polynomial expression a researcher might be interested in applying to data sets. This means expressions with variables and operands such as addition, subtraction, multiplication, and exponentiation can work on the encrypted data as if it was plain text. This flexibility opens an abundance of analytical possibilities.
How To Overcome Limitations Posed By FHE
A brief list of factors hindering the rollout of FHE today would include performance overheads, the lack of standardization, and the limited industry adoption of this cryptographic technology. These are typical of the kinds of obstacles faced by nascent technologies
In our view, most of the hurdles outlined above are connected. As well-crafted FHE hardware and software solutions advance, emerging standards, such as those in the making by FHETCH, will help pave the way to broader adoption of FHE.
On performance, this is precisely where we have seen the application of Application-Specific Integrated Circuits (ASICs) shift the industry paradigm. It is therefore with some hope that we expect to see a major barrier to FHE adoption broken down with the arrival of the first practical, fast, and efficient FHE-targeted ASIC hardware in the coming months.
Research projects and early applications from hyperscalers such as Google, Meta, Amazon, Microsoft and Apple suggest a strong strategic interest in FHE. These organizations are actively exploring FHE and are expected to scale adoption as dedicated FHE accelerators become available.
Importantly, it is expected that large organizations like governments and health agencies will gain the confidence to move forward, too, implementing proven FHE technology to make the best use of the valuable data they hold.
In Summary
Thank you for reading our introduction to the basics of Fully Homomorphic Encryption (FHE) technology. Above, we’ve recounted the concept behind FHE, summed up its early development history, briefly discussed why FHE is the Holy Grail of cryptography, and outlined why large-scale, real-time deployments of FHE have yet to materialize, despite growing interest and early non–real-time implementations. Please stay tuned, though, as this is just the beginning of our FHE technical blog series. Coming up we hope to: discuss the mathematical foundations behind the technology, highlight the current performance issues and performance bottleneck seen in applying FHE, compare the different FHE schemes that are available, and much more.
